As Q4 approaches, businesses – especially startups and SMEs – often juggle increased customer interactions, sales, and administrative tasks. It’s easy to overlook data protection, but failing to safeguard personal data could have significant consequences. For small businesses, remote working presents risks, especially when employees use personal devices or insecure networks. We’ll focus on managing operational data protection risks related to remote working. We’ll outline the key challenges, risks to watch for, and simple steps to mitigate these risks.
Why Remote Working Presents Unique Data Protection Challenges in Q4
The rise of remote working has led to significant flexibility for businesses, but it also brings new data protection risks. Team members, employees or contractors, working from home might use personal devices, unsecured Wi-Fi, or even share files via personal email accounts. All these behaviours can put your business at risk of a data breach or GDPR non-compliance.
Q4 is often a busy period for businesses—particularly retail and services—and these risks are heightened as employees handle more customer data under tight deadlines.
Common risks include:
- Data is accessed via unencrypted personal devices.
- Use of insecure public Wi-Fi to manage business communications.
- Employees storing company data on personal cloud storage platforms.
- Uncontrolled file-sharing practices via personal email or messaging apps.
Key Remote Work Data Protection Risks for SMEs
Let’s break down the most common data protection risks associated with remote working and how they can impact your business.
1. Unencrypted Devices and Inadequate Security Controls
Many team members working from home use personal laptops, phones, or tablets. Without encryption, any data stored on these devices is at higher risk of being accessed by malicious actors in the event of loss or theft.
- Risk: A stolen or lost device could lead to a data breach if sensitive information isn’t encrypted. The ICO (Information Commissioner’s Office) could fine you or damage your business’s reputation.
- Mitigation Tip: Ensure that all devices used for work purposes—company-owned or personal—are encrypted and password-protected. Implement multi-factor authentication (MFA) to add an extra layer of security for accessing company systems.
2. Insecure Wi-Fi Networks
Working from home or in public places may connect to unprotected Wi-Fi networks. Hackers can easily intercept unencrypted data transmitted over these networks, making sensitive customer or business information vulnerable.
- Risk: Sensitive data, such as customer payment information or business contracts, could be intercepted if employees work on insecure networks.
- Mitigation Tip: Advise team members only to use secured Wi-Fi networks. Encourage them to use a Virtual Private Network (VPN), which encrypts data traffic and provides a secure connection, even when using public Wi-Fi.
3. Personal Cloud Storage and File Sharing
Many remote workers use personal cloud storage solutions like Google Drive or Dropbox to store and share work files simply because it’s more convenient than using corporate systems. However, this practice can create significant vulnerabilities if these personal accounts are not secured or don’t comply with GDPR requirements.
- Risk: Personal accounts may not have the same level of security or data protection compliance as business-grade solutions, increasing the risk of unauthorised access to personal data.
- Mitigation Tip: Implement a Bring Your Own Device (BYOD) policy that outlines approved cloud storage solutions for work purposes. Encourage using secure business-grade tools for file sharing, such as OneDrive for Business or Google Workspace, which have stronger security protocols.
4. Inconsistent Data Access Controls
When team members work remotely, monitoring and controlling who can access specific company data can be difficult. If your business hasn’t clearly defined access controls, team members may inadvertently share sensitive information with unauthorised colleagues or third parties.
- Risk: Data could be shared too freely within your company or even leaked outside the business if employees aren’t clear on who should access what.
- Mitigation Tip: Regularly review your access control policies and ensure employees understand the data they are authorised to handle. Set up systems where only specific individuals can access sensitive customer data or personal information.
Mitigating Remote Working Data Protection Risks in Q4
To minimise these risks, SMEs should adopt a proactive approach to data protection. Here are some practical steps you can take right now to improve your remote work security:
1. Encrypt Devices and Data
Ensure that all devices, whether personal or company-owned, are encrypted. If team members use personal devices, provide guidance or tools to help them enable encryption and secure their data. Most modern operating systems (Windows, MacOS, iOS, Android) have built-in encryption features that are easy to activate.
2. Implement Secure Remote Access
Use a VPN for secure access to company systems. This ensures that data transmitted between remote team members and your business’s servers remains encrypted, even over public Wi-Fi. Many VPN providers offer affordable options for small businesses.
3. Develop a BYOD Policy
Create a Bring Your Own Device (BYOD) policy that outlines the rules for using personal devices for work. This policy should cover acceptable use, security requirements (like mandatory encryption), and protocols for reporting lost or stolen devices.
4. Choose Secure File-Sharing Solutions
Standardise the file-sharing process within your company by adopting a business-grade cloud solution like Google Workspace or Microsoft OneDrive. Ensure these platforms are configured with security measures such as MFA and limited access controls.
5. Regularly Review and Update Data Access Controls
Regularly audit your data access permissions to ensure that only necessary personnel can access sensitive data. Conduct quarterly reviews to remove access for team members who no longer require it and ensure that new staff are correctly assigned permissions.
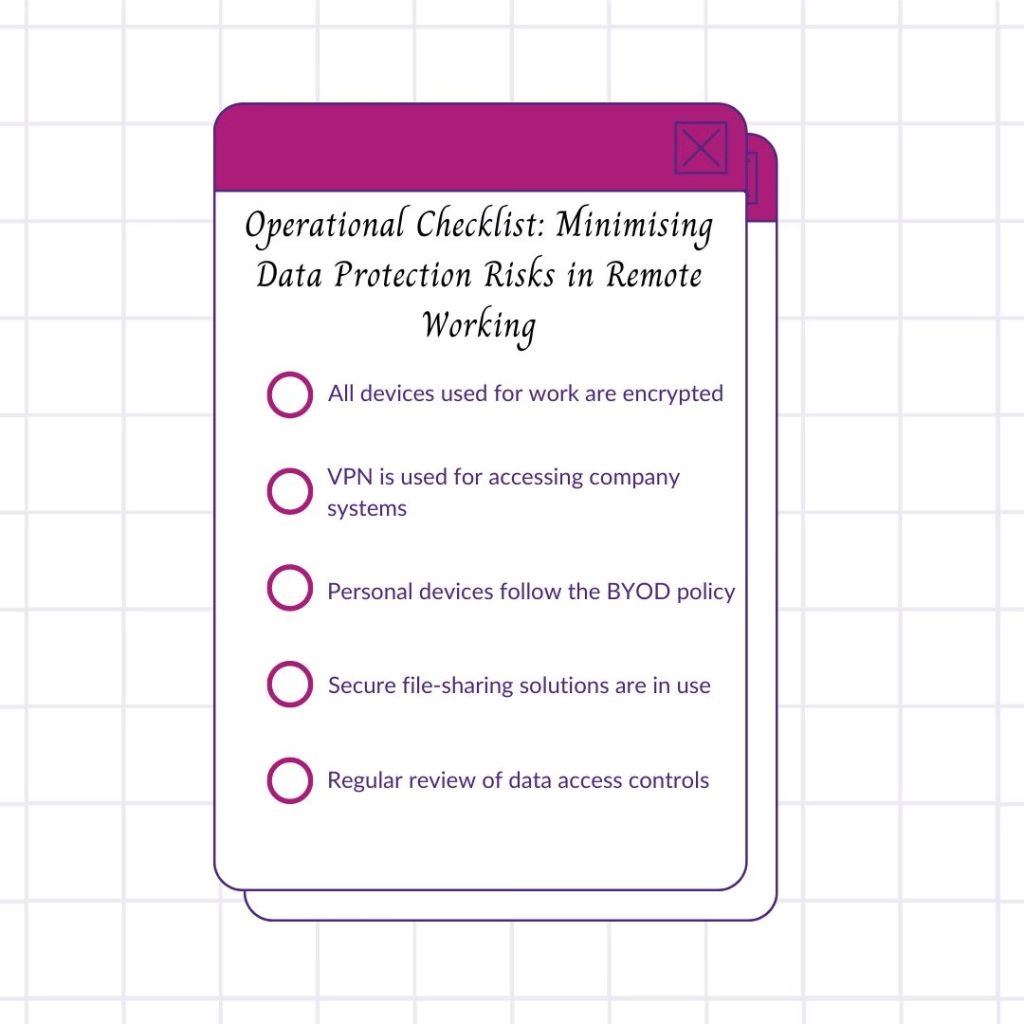
Operational Checklist: Minimising Data Protection Risks in Remote WorkingHere’ss a quick checklist to help you assess your current remote work data protection practices:
Feel free to download this checklist [here] (link to download) to help manage your remote data protection risks throughout Q4.
Common Remote Working Data Protection Mistakes
Here are some common mistakes SMEs make when it comes to remote working and data protection and how to avoid them:
1. Using Personal Email for Work Files
- Risk: Personal email accounts are often less secure than business email platforms, and they can easily expose sensitive information to hackers or lead to data loss.
- Solution: Always use business email addresses and secure file-sharing tools to transmit work files.
2. Assuming Home Networks Are Secure
- Risk: Team members may assume their home Wi-Fi is safe, but it can be vulnerable to hacking unless secured with strong passwords and encryption.
- Solution: Train employees (or advise contractors) on securing their home networks or providing them with VPN access.
3. Neglecting to Report Lost Devices
- Risk: Failure to report lost or stolen devices can delay responses to potential data breaches.
- Solution: Create clear policies requiring employees to report lost or stolen devices immediately and establish a procedure for remote wiping or disabling.
Final Thoughts: Protecting Your Business in Q4
Q4 can be a hectic time, but by proactively managing the data protection risks associated with remote working, your business can avoid costly data breaches and stay compliant with GDPR. Implementing strong security measures—like encryption, VPNs, and secure file sharing—will reduce operational risks and ensure your business handles sensitive data responsibly.
If you need help setting up secure remote working systems or auditing your current setup, book a free clarity call consultation or sign up for our newsletter to receive practical data protection tips in your inbox.
Why not read some of our other blogs:
- Preparing for Q4: Data Protection Audits Tips
- Essential Summer Data Protection Tips for Small Businesses
- Top 10 Myths About Data Protection and Small Businesses
- How to Keep Your Business Data Safe This Summer: Practical Tips
- Data Protection and Working Virtually